The Unique Critical Infrastructure Cybersecurity Ecosystem
Cyberthreats to critical infrastructure organizations are growing, and protecting these essential facilities is a complex endeavor. Traditional work methods in which each department focuses on their own specific silo are putting critical infrastructure in graver danger. OT networks are the last line of defense protecting physical assets and they cannot be properly protected without working hand in hand with the IT department.
It is not, however, collaboration just between these two departments that will best serve to protect the critical infrastructure industry from cyberattacks, but rather a three-pronged critical infrastructure network involving IT and OT departments, inter-organizational collaboration and regulators that can all work together to strengthen the defense, weaken the attackers and ensure that all activity is in line with regulations.
This article will explain why collaboration is so necessary yet fraught with so many challenges as well as describe the three circles of collaboration that will be key to protecting this crucial sector.
Two Heads are Better Than One
Information sharing and working together is crucial in order to protect critical infrastructure from the threat of cyber attacks. It is no secret that the “dark web” is full of hackers sharing their secrets, including their best tips and even their failures in order to strengthen their community and make it easier to complete successful cyberattacks. CISOs around the world are jealous of the community that these hackers have built. They recognize that if the “good guys” were half as good at sharing information among themselves, they would be in a much better position to learn from each other's experiences and stay several steps ahead of the hackers.
Why is Collaboration Such a Challenge?
Unfortunately, the parties whose collaboration is required are not used to working together. IT and OT departments each focus on their own objectives. Given IT’s strict focus on protection and OT’s clear mandate to keep the systems up and running, they are often in direct conflict with each other, making collaboration complicated.
CISOs at different critical infrastructure organizations are loath to share their experiences for fear of repercussions should they admit to having been the victim of a cyberattack. The very information that could prevent further attacks at other locations is often buried instead of being shared.
And, the third piece of the puzzle - the regulators - are often seen as a nuisance adding additional burdens to companies, especially in the field of cybersecurity where those in the business sector are not subject to all of the same regulations as critical infrastructure, so it is something unfamiliar and new for the CISOs to handle.
If each of the parties involved in the 3 collaboration circles looks at the big picture and understands how each of their roles fits together, they will realize that they are all working towards the same goal of ensuring the cybersecurity of critical infrastructure. They will be able to reach this goal much faster and more effectively if they collaborate.
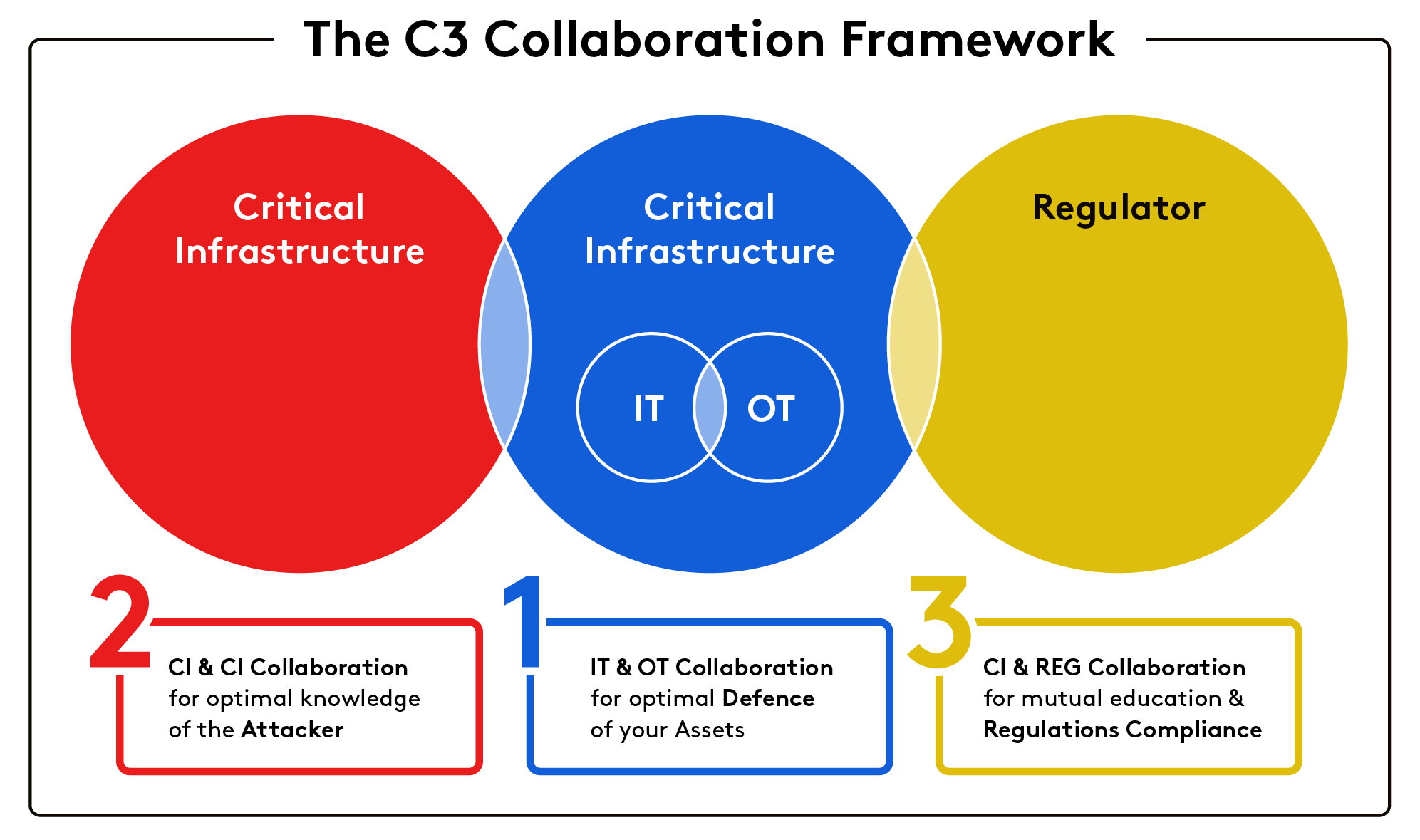
The three collaboration circles are:
1) IT and OT within the same organization
2) different critical infrastructure companies working together and
3) regulators working with critical infrastructures. Each circle will make its own contribution to the overall process in the following ways.
Strengthening Defense with The IT-OT Connection
Most cyberattacks began with a covert penetration via the IT network and from there gain access to the OT network where the major risks lie. Strengthening the first line of defense is of the utmost importance and full protection requires full collaboration between the IT and OT teams. A major mindset and cultural shift is needed to take these teams from siloed behavior to working together to create and implement a unified cybersecurity strategy.
Weakening Attackers by Sharing Inter-Organizational Knowledge
As each critical infrastructure organization becomes more collaborative internally, they must also develop ways to collaborate and share information with other critical infrastructure facilities. They are all at risk of attack, most likely from the same attackers who will use similar methods and who have their own networks of information-sharing that make them stronger. By openly sharing information about attempted (or even successful) attacks, the entire ecosystem will gain a better understanding of the attackers’ patterns and newest methods faster, making it easier to preempt them. Creating peer-to-peer networks can help facilitate ongoing communication, but this type of information sharing will also require somewhat of a cultural shift within critical infrastructure organizations.
Staying in Compliance by Working with Regulators
Cybersecurity experts that move from the private sector to the critical infrastructure world are not necessarily used to all of the regulations that critical infrastructure organizations are subject to. And, cybersecurity is a new and unfamiliar topic to the regulators. This mutual lack of knowledge combined with the fact that regulators are generally seen as intimidating figures who are there to make life more difficult is a recipe for disaster. The reality is that if critical infrastructure managers and regulators put their preconceived notions aside and work together, there is a tremendous opportunity for them to prevent cyberattacks. The critical infrastructure cyber team can educate the regulators about the reality of the threats and what is needed for protection so that they can work together to create the best strategy that works within the confines of legal regulations.
In Summary
As hackers become more daring and more skilled, critical infrastructure facilities around the world are at great risk of being attacked, the results of which can be catastrophic. Governments and managers of critical infrastructure are starting to realize the severity of the situation and are looking for the right action to take to protect these critical services. For example, the United States Department of Homeland Security has recently implemented a public-private partnership approach in which they are encouraging significant coordination and collaboration between the public and private sectors to ensure that knowledge is being shared and the key stakeholders are working together.
This is an approach that will serve the entire critical infrastructure industry well. By bringing together everyone involved in running and protecting these crucial facilities, and sharing information both internally and externally, a strong defense can be built. With the right training, all parties involved can gain a thorough understanding of each other’s roles and how those roles can complement each other to create and implement one comprehensive cybersecurity strategy.






